What is information security?
According to dictionary.com, information security refers to “the state of being protected against the unauthorized use of information, especially electronic data, or the measures taken to achieve this.”
In essence, information security refers to the tools and processes that organizations use to protect information, to ensure that data is kept secure from unauthorized access or alterations.
Such tools and processes can include print, electronic, or any other form of confidential, private and sensitive information or data from unauthorized access, use, misuse, disclosure, destruction, modification, or disruption.
Why Information Security is important in business?
You want to protect your business and employees. Your employees have their personal data in your hands. There have been many fraud cases where people have made use of other employees’ data for their own benefit. Here’s how you can spot and prevent HR fraud in your department. Also, if you are a service based business, your customers likely also have provided you with some of their personal data. In this digital age, hackers, viruses and more are constantly implementing new ways to hack your system. Hence, it is important to be able to combat them.
When you have good information security in place, you will be protected against the unauthorized use of information, especially electronic data, or the measures taken to achieve this.
Why Information Security is important for a software provider like Krowme?
It is important for companies like Krowme to be compliant with information security best practices. Krowme provides HRMS products and hence, the customers who use Krowme products are going to be uploading sensitive data about their employees to the Krowme platform. The sensitive data mainly refers to the employee’s personal details (age, date of birth, leave date, employee address, personal email address, identification number, appraisals, next-of-kin contact, and more).
Therefore, having top-notch security is a top priority at Krowme. This is why Krowme is now ISO 27001 certified and will always put security as a top priority.
However, simply having secure software is not enough to ensure that your information security is as virus-proof and hacker-proof as possible. You need to also take measures to educate your colleagues about the importance of information security.
If you do not educate your colleagues and set protocols for them to adhere to, there is still a high chance of your organization getting exposed to hackers, viruses and more.
Here are 4 key categories of information security best practices that you can start implementing now.
1. Information Security Best Practices For Your Office Space
1a. Office Printer
All documents are to be cleared from printers immediately when printed. This is to ensure that any confidential documents are only seen by the right people.
1b. Server Share Folder
The Server share folder is used to communicate documents across departments.
Here are some pointers you need to take note of to ensure that your server share is as secure as possible.
- When recipient has retrieved a confidential document, the depositor has to remove it as soon as possible.
- Always do a periodic spring clean of the server share folder and ensure that ALL confidential documents are either removed immediately or password-protected.
- Where confidential files are required to be shared via server share, ensure that they are encrypted.
1c. Your Desk Area
In addition to being cautious online, you also need to take the steps mentioned below to ensure that your office desk area is cleared of all unnecessary breaches to your information security.
i. Clear Desk
- Keep sensitive (classified) hard copy documents away from view or locked in a storage cabinet
- Working desk to be cleared everyday
- No visible information (esp. passwords) to be pinned or stuck to your desk/monitors.
ii. Protect Your Monitor Screen
- Ensure access to your laptop(s) are password protected
- Enable activation of screen savers within 10 minutes of user inactivity
- When leaving for lunch break, always activate lock screen
- At the end of each day, all are expected to shut odown and log off network resources.
2. Information Security Best Practices for Your Work Email
2a. Set a secure password For all work-related email accounts
When do you need to use a password?
You need a password to:
- Access network
- Access ema.il
- Access applications
- Access hardware device (external hard drives, laptops, mobile devices)
- Access to confidential documents
As you can see, a password is required to access everything that you own (or is linked to you) on the web.
What does a strong password look like?
Here are examples of weak passwords:
- Qwerty
- 1passw*rd
- Opensoft12#
Here is an example of a strong password:

What is the ‘formula’ of a good password?
- Minimum 12 characters and contains characters from the following four categories:
- Upper case (A through Z)
- Lower case (a through z)
- Digits (0-9)
- Special characters (!,$,#,%, etc.)
- Should not contain personal identifiable information.
How do you protect your password?
- Never share personal account passwords
- Change your password once every 3 months, or as frequently as possible
- Do not leave records of password at work area
- Avoid including personal info in your password that can be easily guessed
2. Email Guidelines
2b. Add a disclaimer to your email signature for the intended recipient to take note of
It is important to set a disclaimer to your email as this will help the intended recipient to understand that you take your security very seriously.
Here is a standard disclaimer liner that you can place in your email signature for all emails that you send out:
“The information contained herein (including attachments) is classified and is intended solely for the addressee(s). If you are not the intended recipient, please notify the sender immediately and delete this message. Any unauthorized use of this message or any accompanying document is strictly prohibited and any such action may result in legal proceedings. YOURCOMPANYREGISTEREDNAME does not guarantee and is not liable for the security of any information electronically transmitted, or for the proper and complete transmission of the information contained in this communication, or for any delay in its receipt.”
2c. Be wary of incoming emails
Always check for attachments and sender’s email address before downloading or clicking any attachments.
Examples of suspicious emails
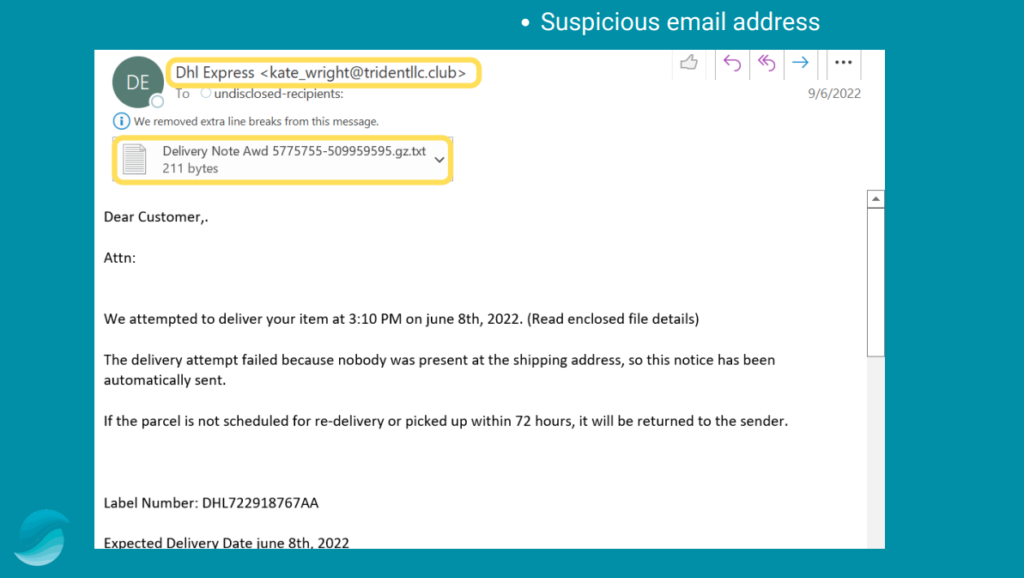
i. The screenshot below shows an example of a suspicious email attachment. The email address also looks suspicious.
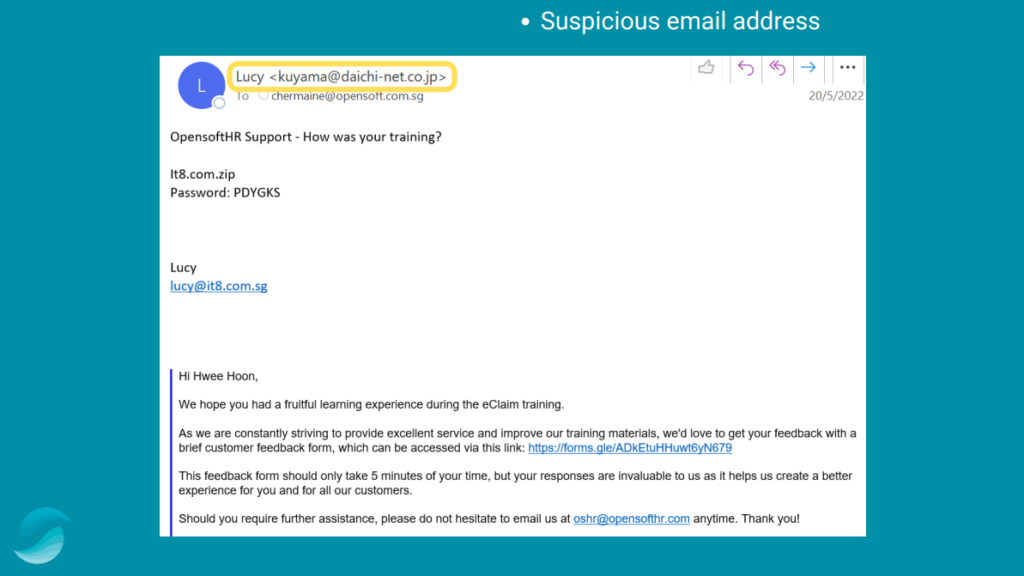
ii. The screenshot below shows an email where the email address looks suspicious. The email also contains a url that looks questionable and a password to log into that url. The url and password have no relation with the content in the email.
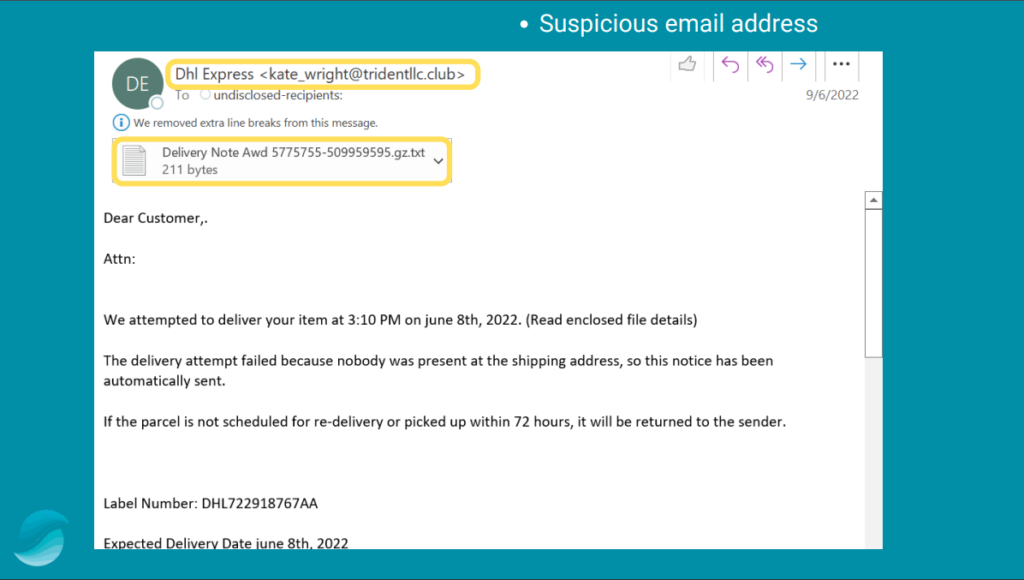
iii. The email below is from a suspicious email and also has an email attachment. When you receive such emails from questionable email addresses, NEVER open the attachments as there is a high chance that the attachments are viruses.
2d. Set passwords for confidential documents
If you have any files that are confidential, it is best to secure those files before you send them to the recipient. Find out how you can password-protect your files for free using 7-Zip.
Avoid downloading any software (including free and shareware) onto the company network without explicit permission from the IT department.
3. Best Information Security Practices to secure your own devices
- When using your own devices during work hours, at office or when teleworking, please use it for work-related purposes only (personal matters not allowed)
- Ensure that you have an anti-virus software installed on your own device if you are using your own work devices for work-related purposes
- If using your own devices to access company networks and applications, please follow the same rules that apply to your organisation’s internet usage policy.
4. Remote Working Best Information Security Practices
‘Do’s of Teleworking
- Access to Company network & applications can be attained via a secure VPN, which must be authorised/provided by the IT department.
- When not in use, please logout and close browsers after use to prevent potential hackers.
‘Don’t’s of Teleworking
- Do not attempt to log on the Company network via VPN using public Wi-Fi (especially if it’s free).
- Do not share/loan devices with unauthorised users. This includes unauthorised staff, family, friends and other members of the public.
- Do not share username/password and login credentials with unauthorised users. This includes unauthorised staff, family, friends and other members of the public.
Good Information Security Practices At Work
Download the ‘Good Information Security Practices At Work’ white paper to find out about the 4 main workplace categories that are mandatory for you to implement good information security practices.
ISO 27001 Certified
Krowme is ISO 27001 Certified. This means that we have been officially certified to adhere to the information security guidelines stated above and everything else that is required under ISO 27001. This means that when it comes to our modules, office processes and ethics, the security at Krowme is of a top notch standard.
Reach out to us anytime to get a quote to improve the workplace operations of your business.
Reach out to us anytime to get a quote to improve the workplace operations of your business.




Leave a Reply